We are picking up from the first part of this post, HERE.
Enable/Configure/Disable iSCSI CHAP
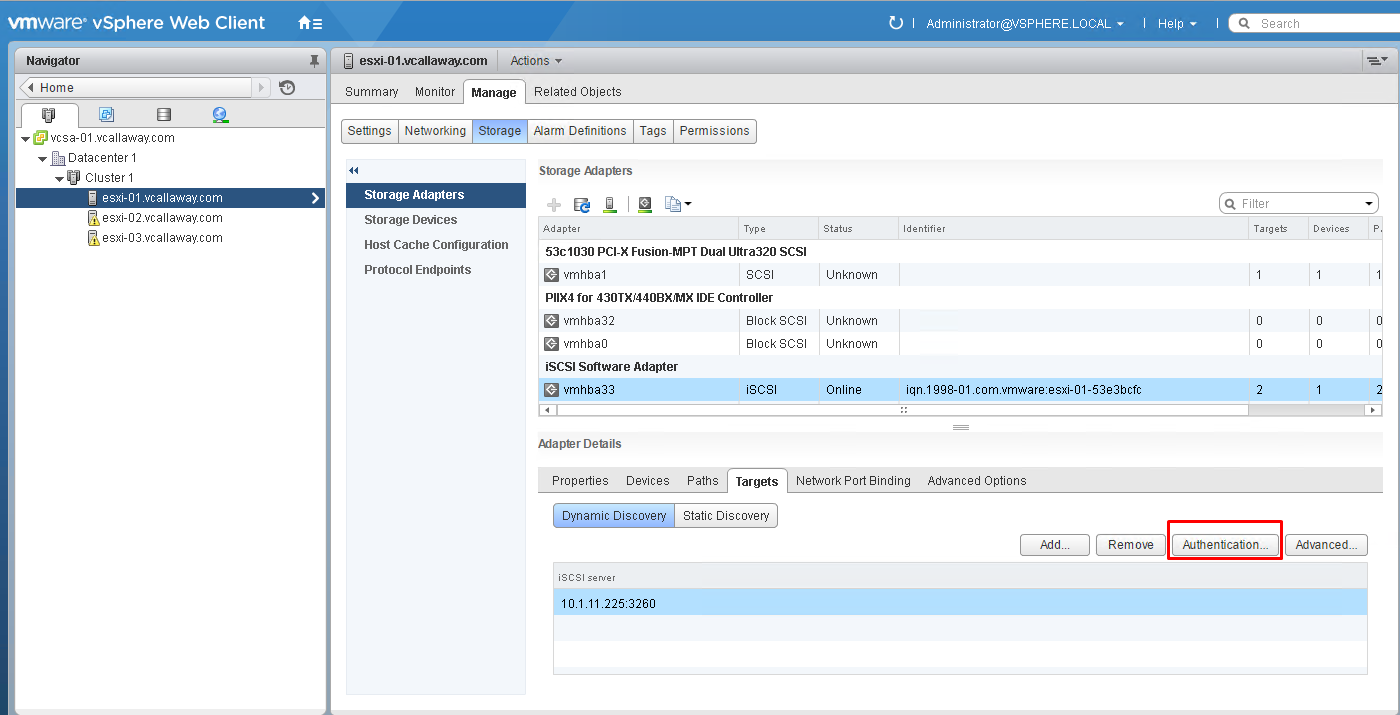
Host > Manage Tab > Storage Adapters > select initiator > Targets tab > Authentication.
Note: I’m not using authentication or any ACL’s for my storage security as this is a lab environment. It is best practice to use some sort of ACL, CHAP security mechanism in production environments.
Note: There are 4 options to configure CHAP
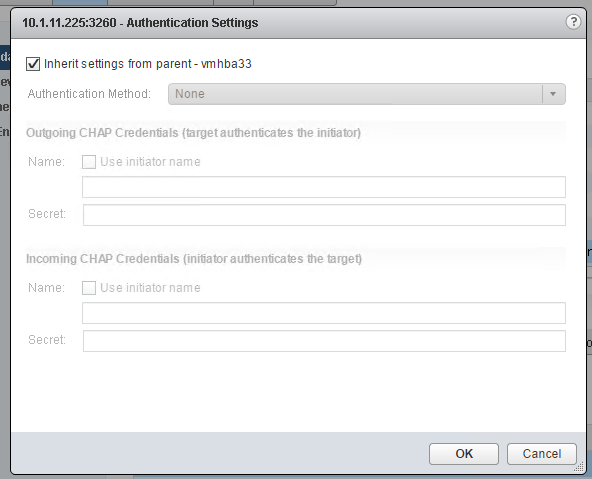
- Unidirectional CHAP required by target (Storage)
- Unidirectional CHAP unless prohibited by target (Storage)
- Unidirectional CHAP
- Bidirectional CHAP
Determine Use Cases for Fiber Channel Zoning
- Limit number of targets/LUNs presented to a host/initiator.
- Network segmentation, similar to that of VLANs
- Preferred paths in a fabric.
Compare/Contrast/ Array Thin Provisioning vs. Virtual Disk Thin Provisioning
Array Thin Provisioning happens on the Storage Level/LUN.
Virtual Disk Thin Provisioning happens on the and within the Virtual Machines virtual disk.
To continue to the next objective, click HERE.