Objective Topics:
- Describe SSO architecture and components
- Differentiate available authentication methods with VMware vCenter
- Perform a multi-site SSO installation
- Configure/Manage Active Directory Authentication
- Configure/Manage Platform Services Controller (PSC)
- Configure/Manage VMware Certificate Authority (VMCA)
- Enable/Disable Single Sign-On (SSO) Users
- Upgrade a single/multi-site SSO installation
- Configure SSO policies
- Add/Edit/Remove SSO identity sources
- Add an ESXi Host to an AD domain
Describe SSO architecture and components
vCenter SSO is an authentication broker and security exchange infrastructure that is apart of the Platform Services Controller or PSC.
vCenter Single Sign-On Handshake for Human Users
- User logs into vSphere Web Client with username/password. (entering manual credentials or windows auth)
- vSphere Web Client passes the login info to the vCenter SSO service, which checks the SAML token of the vSphere Web Client, if valid token exists, vCenter then checks whether the user is in the configured identity source (ie…Active Directory)
- If only user name is used, SSO checks the default domain.
- If a domain name is included with the username (domain\myuser or user@domain), vCenter SSO checks that domain.
- If user can authenticate to ID source, vCenter SSO returns token that represents the user to the Web client.
- vSphere Web Client passes the token to the vCenter Server
- vCenter Server checks with the vCenter SSO server that the token is valid and not expired.
- vCenter SSO server returns the token to the vCenter Server, using the vCenter Server Authorization Framework to allow user access.
vCenter SSO Components:
- STS (Security Token Service)
- Administration Server
- VMware Directory Service (vmdir)
- Identity Management Service
Source: vSphere 6 Security Guide
Perform a multi-site SSO installation
Refer to KB Article 2034074
Configure/Manage Active Directory Authentication
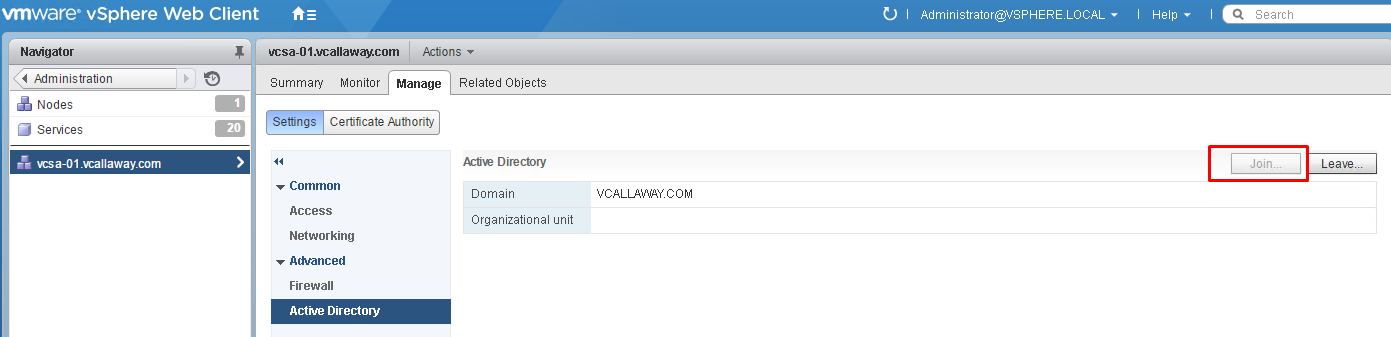
Adding vCenter Server to Active Directory Domain
Administration > vCenter Server > Manage Tab > Active Directory
I’ve already joined my vCenter, but you’ll click ‘Join’ and enter valid AD credentials for your domain.
Once complete vCenter Server will need to be rebooted. (Standalone).
Adding ESXi Hosts to Active Directory Domain
Select ESXi Host > Manage Tab > Authentication Services
Click ‘Join Domain’. Enter Domain, and valid domain credentials. No reboot is required.
Another way to verify is to check for the computer objects in Active Directory.
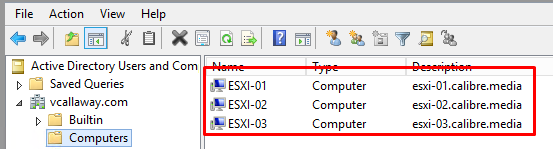
This can be done for vCenter as well. Pretty straight forward.
Configure/Manage Platform Services Controller (PSC)
Login to PSC by using the vCenter FQDN or IP Address and append /PSC to the URL. Make sure you use the administrator@vsphere.local account.
Example: https://vcsa01-vcallaway.com/psc
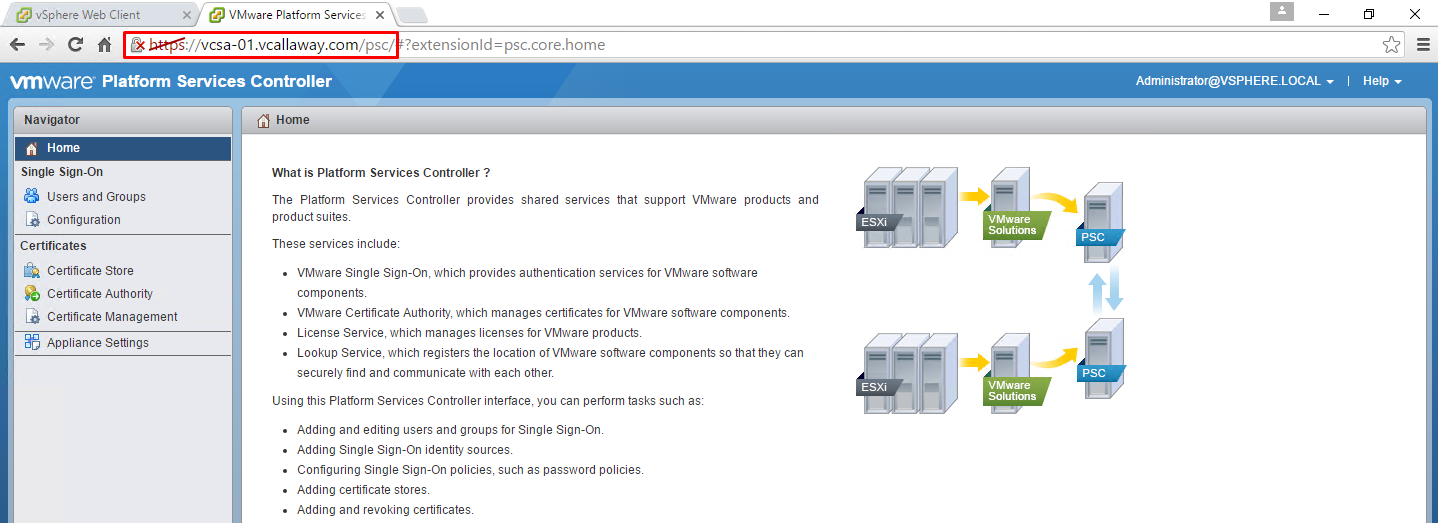
Options Available:
- SSO users/groups to add/change
- Adding Identity Sources
- Managing Certificates
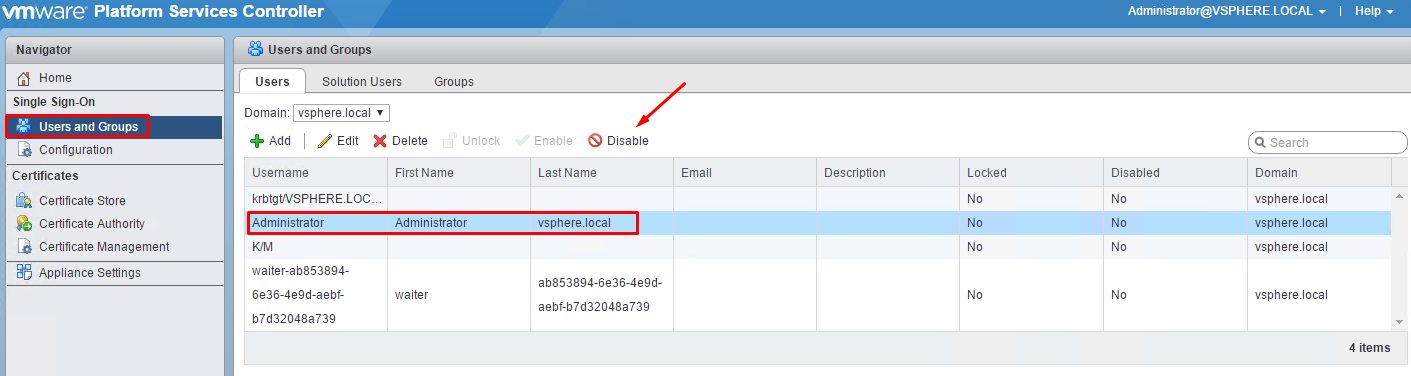
Enable/Disable Single Sign-On (SSO) Users
Upgrade a single/multi-site SSO installation
Will make post in separate post.
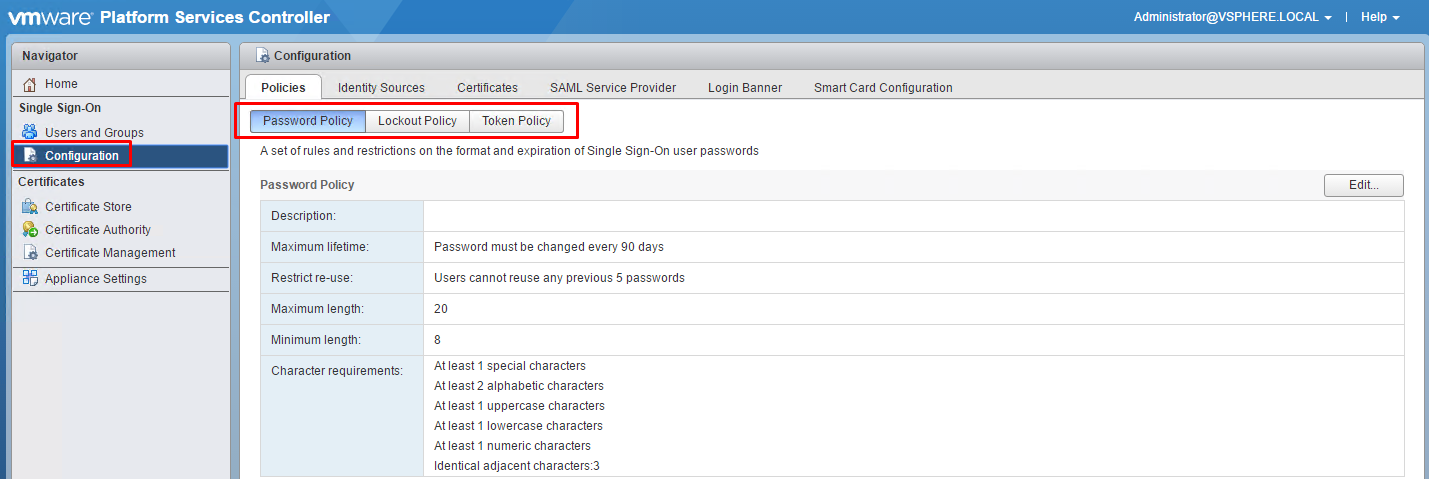
Configure SSO policies
Policies are: Password Policy, Lockout Policy, Token Policy
Add/Edit/Remove SSO identity sources
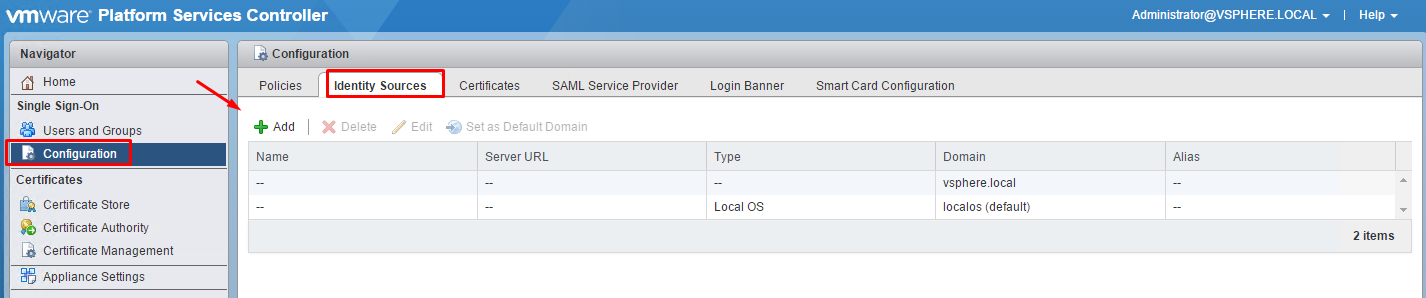
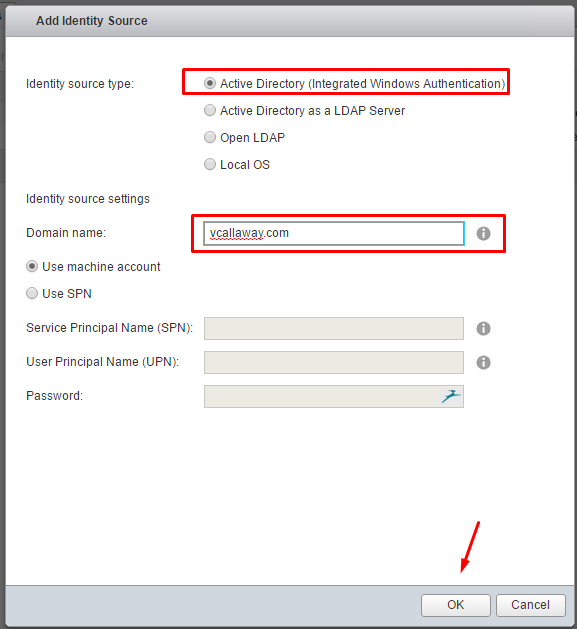
Select how you want to communicate to the Identity Source. I’ll use ‘Active Directory (Integrated Windows Authentication), since the vCenter Server is joined to the domain. Additionally you can use Active Directory as an LDAP Server if the vCenter Server is NOT part of the AD domain or Open LDAP or Local OS.


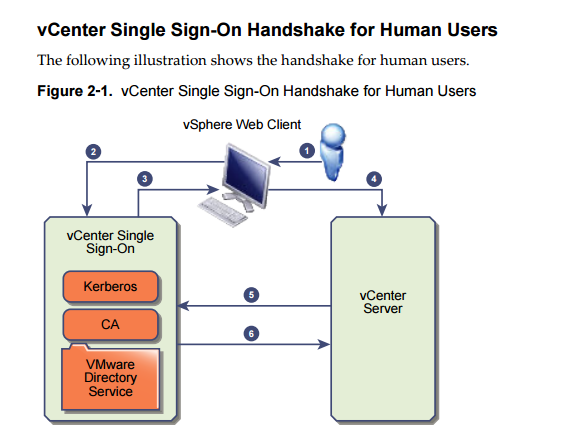
This is one of the best blog after any book ( which covers complete architecture) to explain in simple way how SSO architecture broadly looks like with its component and i always keep in my get pocket as favorite link.