This objective is continued from this previous post, HERE.
Migrate virtual machines to/from a vSphere Distributed Switch
Unfortunately I’ve already moved all my standard switches over to Distributed switches prior to this study guide.

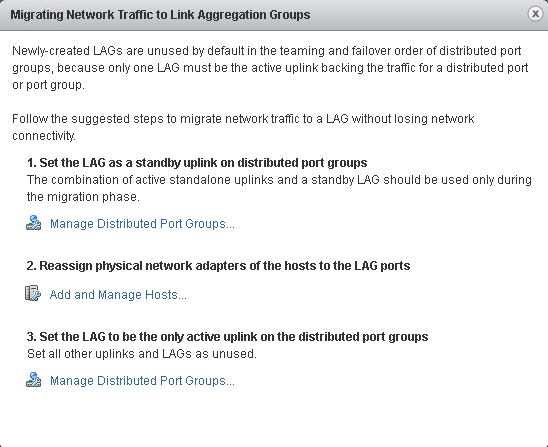
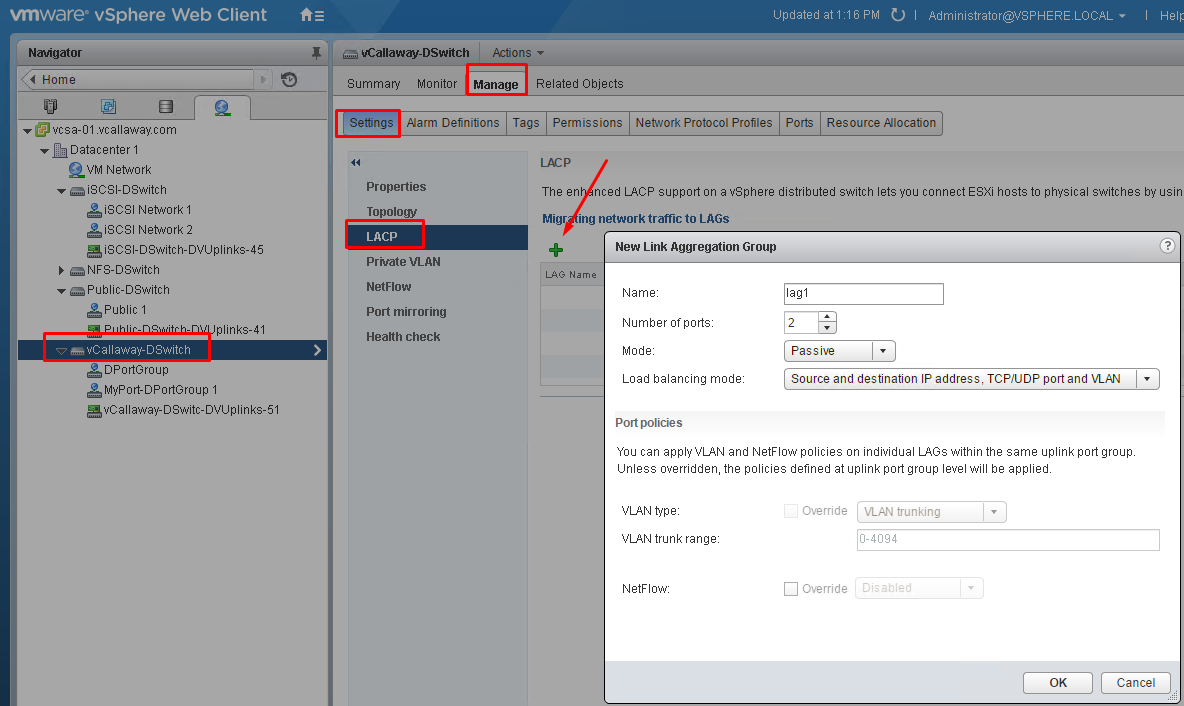
Configure LACP on vDS given design parameters
I can’t demonstrate migrating to LACP uplinks since I’m using VM Workstation, we can however see where we would configure that.
Note: Link Aggregation Control Protocol (LACP) can only be configured through the vSphere Web Client.
Helpful guide from VMware Web Client
Creating the LACP link.
More information about vSphere 6 LACP networking, see the VMware Networking Guide.
Describe vDS Security Polices/Settings
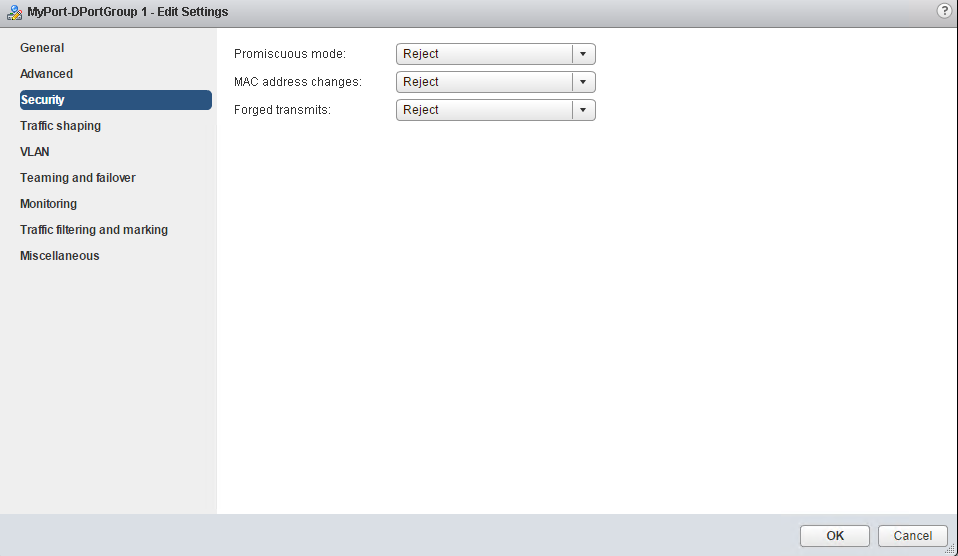
There are three network security policies on vDS. Those are promiscuous mode, MAC address changes and Forged transmits.
- Promiscuous Mode – Default settings are set to REJECT for both (VSS and VDS). If changed to ACCEPT then the guest OS can receive ALL traffic which passes through that particular vSwitch or Portgroup.
- MAC address change – Default setting is REJECT for VDS but accept on VSS. If set to ALLOW then the host accepts requests to change the effective MAC address to a different one than the original.
- Forged transmits – The default settings is REJECT for VDS but ACCEPT on VSS. The host do not compare source and effective MAC addresses which are transmitted from a VM. REJECT protects against MAC Impersonation.
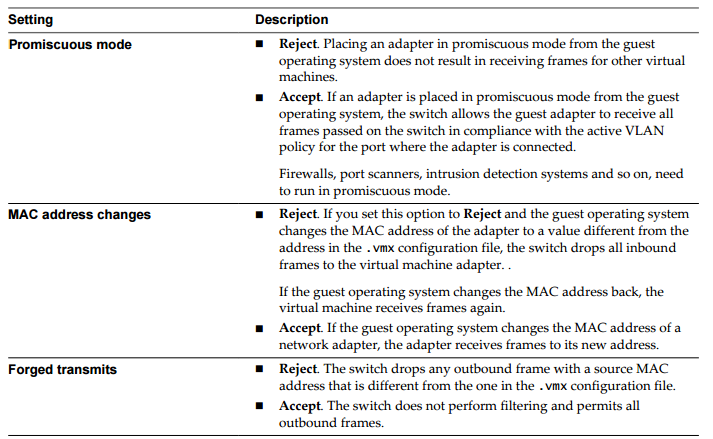
Source: VMware Networking Guide & Vladan.fr
vDS Security Polices can be applied at 2 different location.
- Per DPortGroup
- Per Individual Port
Location for Policies/Settings for the vDS
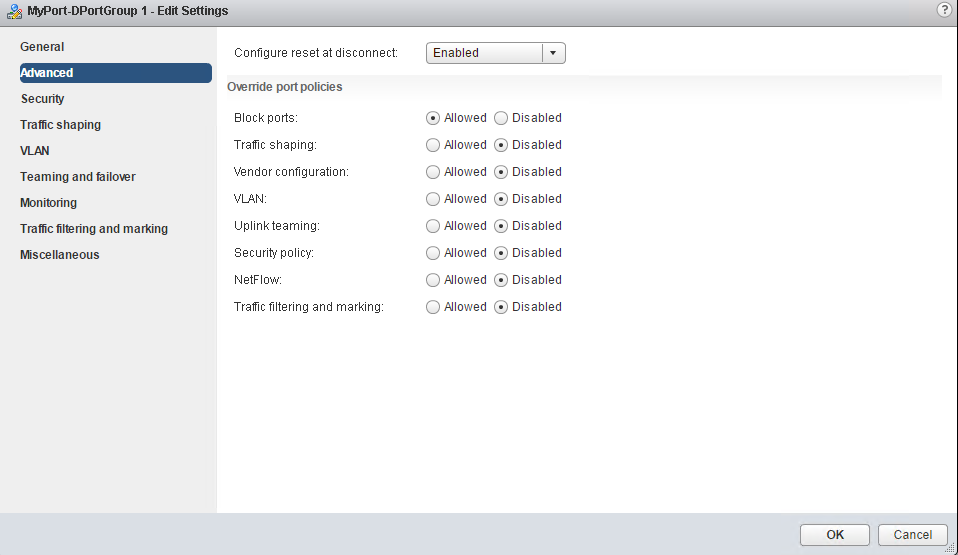
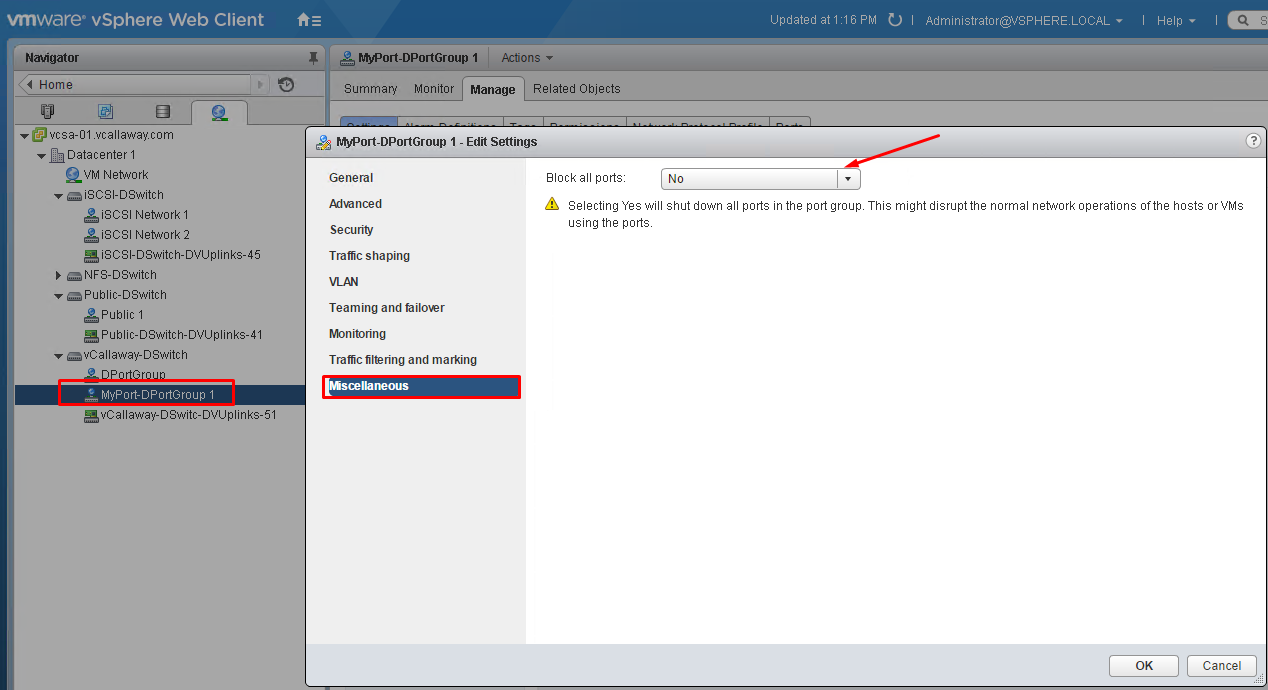
Configure dvPort group blocking policies
Be sure to read the warning. Changing this could have a very big impact on your VM communications.
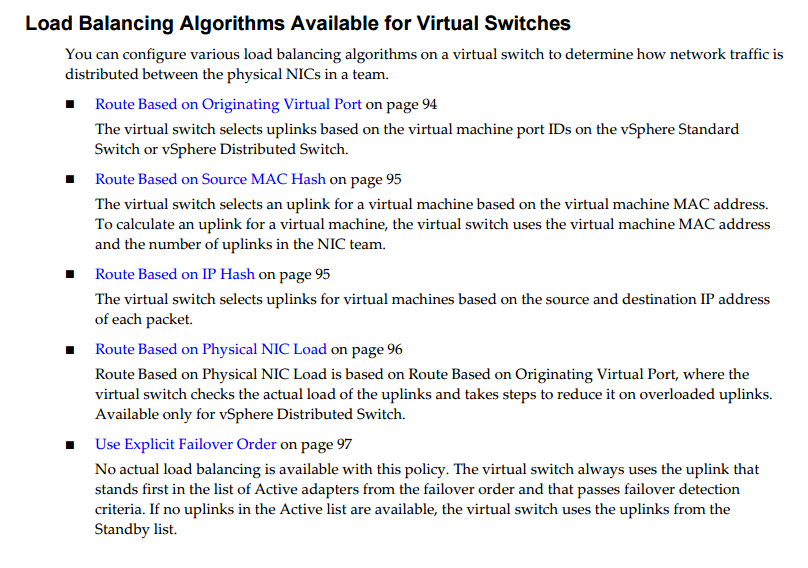
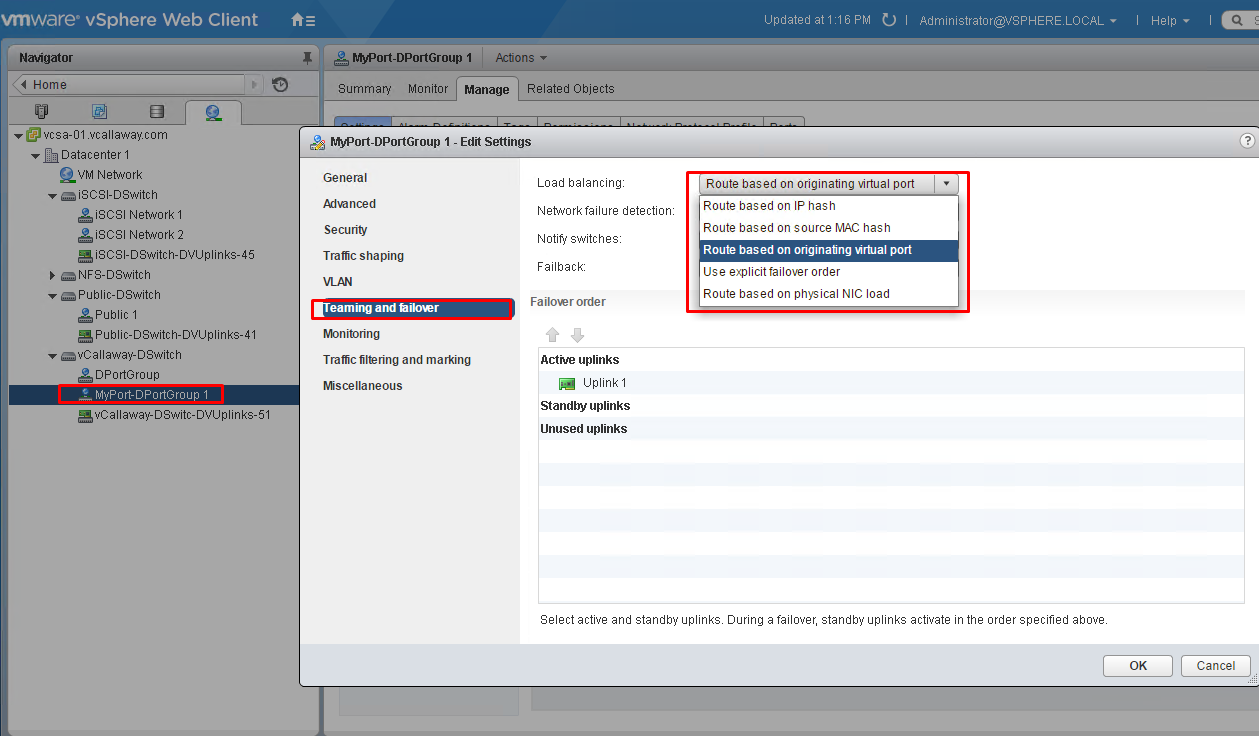
Configure load balancing and failover policies
Source: VMware Security Guide (Page 93)
This Objective continues on a new post HERE.