Objective Topics:
- Harden ESXi Hosts
- Enable/Configure/Disable services in the ESXi firewall
- Change default account access
- Add an ESXi Host to a directory service
- Apply permissions to ESXi Hosts using Host Profiles
- Enable Lockdown Mode
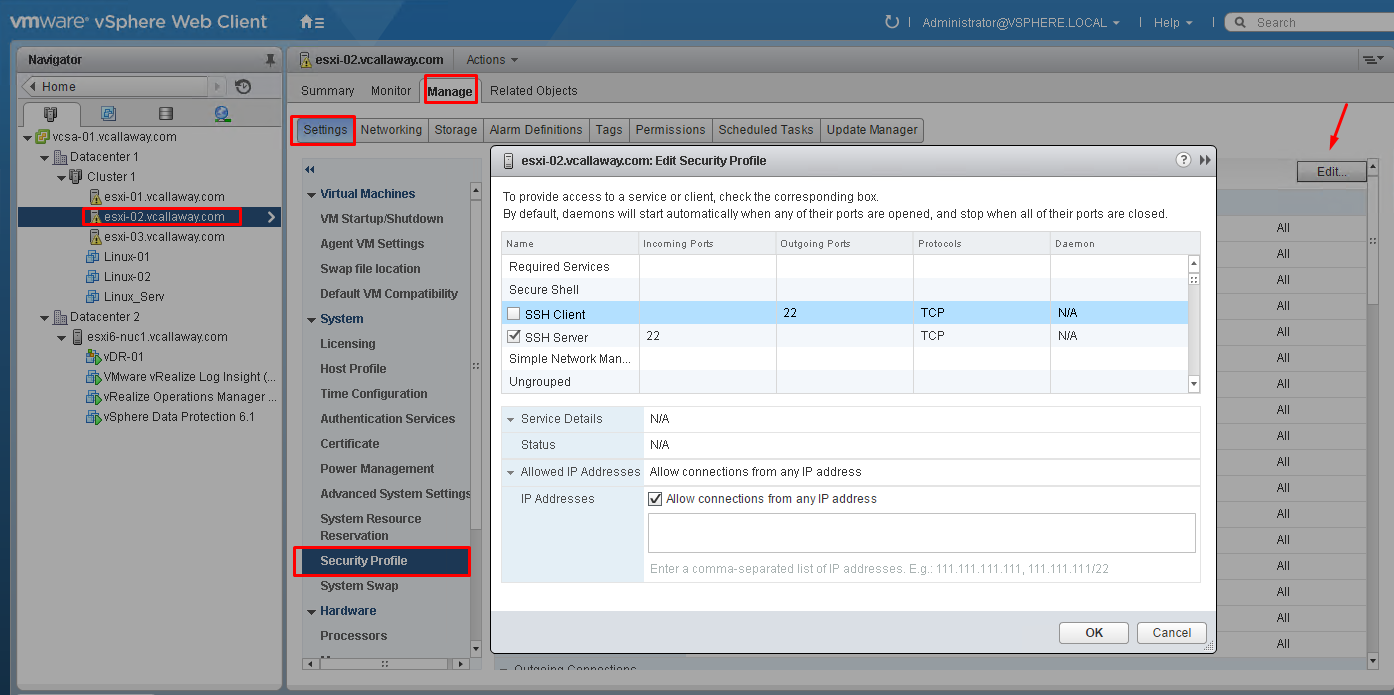
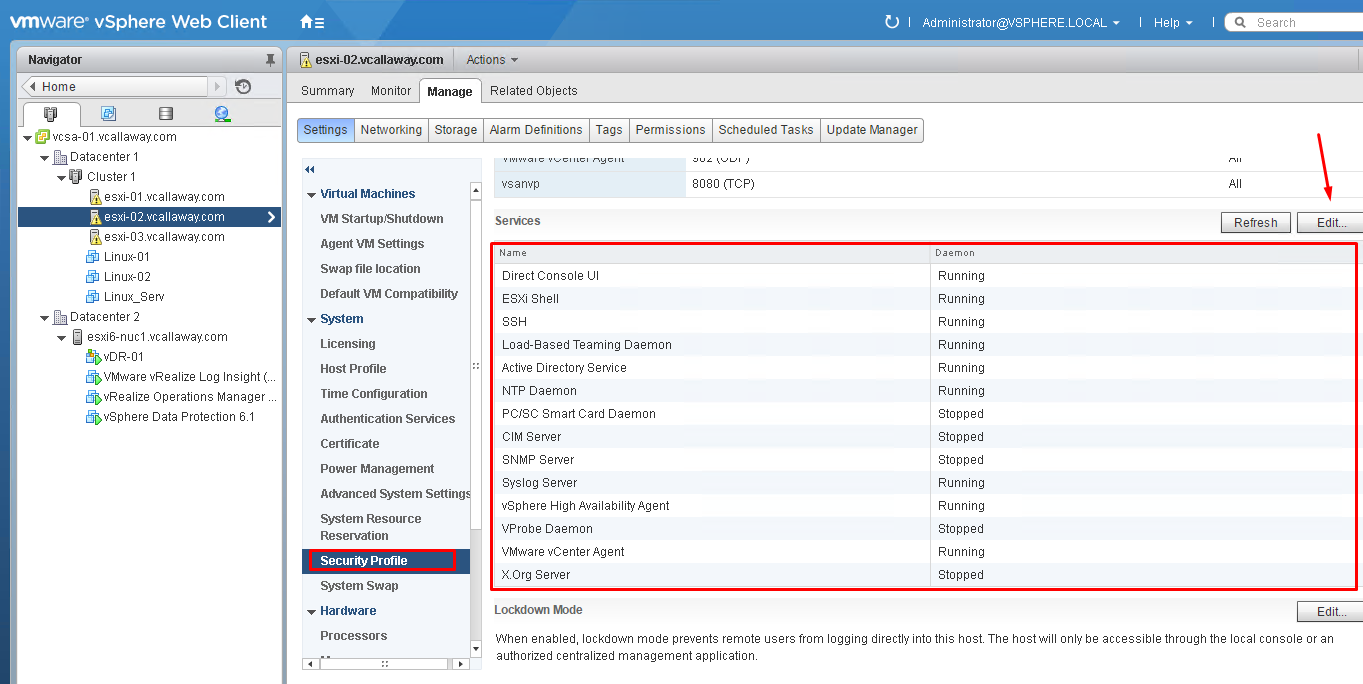
- Control access to hosts (DCUI/Shell/SSH/MOB)
- Harden vCenter Server
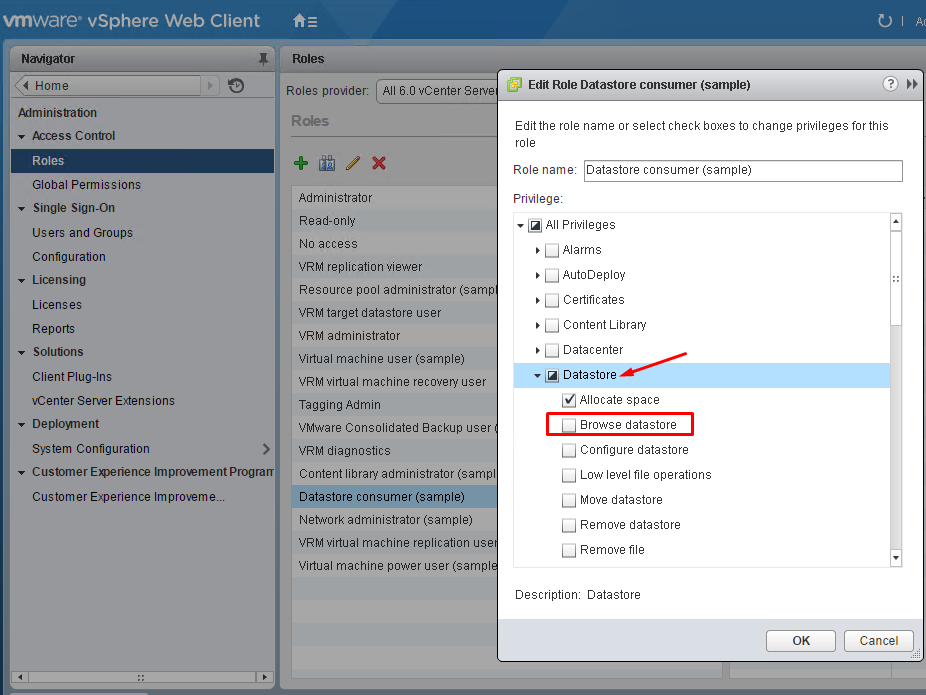
- Control datastore browser access
- Create/Manage vCenter Server Security Certificates
- Control MOB access
- Change default account access
- Restrict administrative privileges
- Understand the implications of securing a vSphere environment
Harden ESXi Hosts
Enable/Configure/Disable services in the ESXi firewall
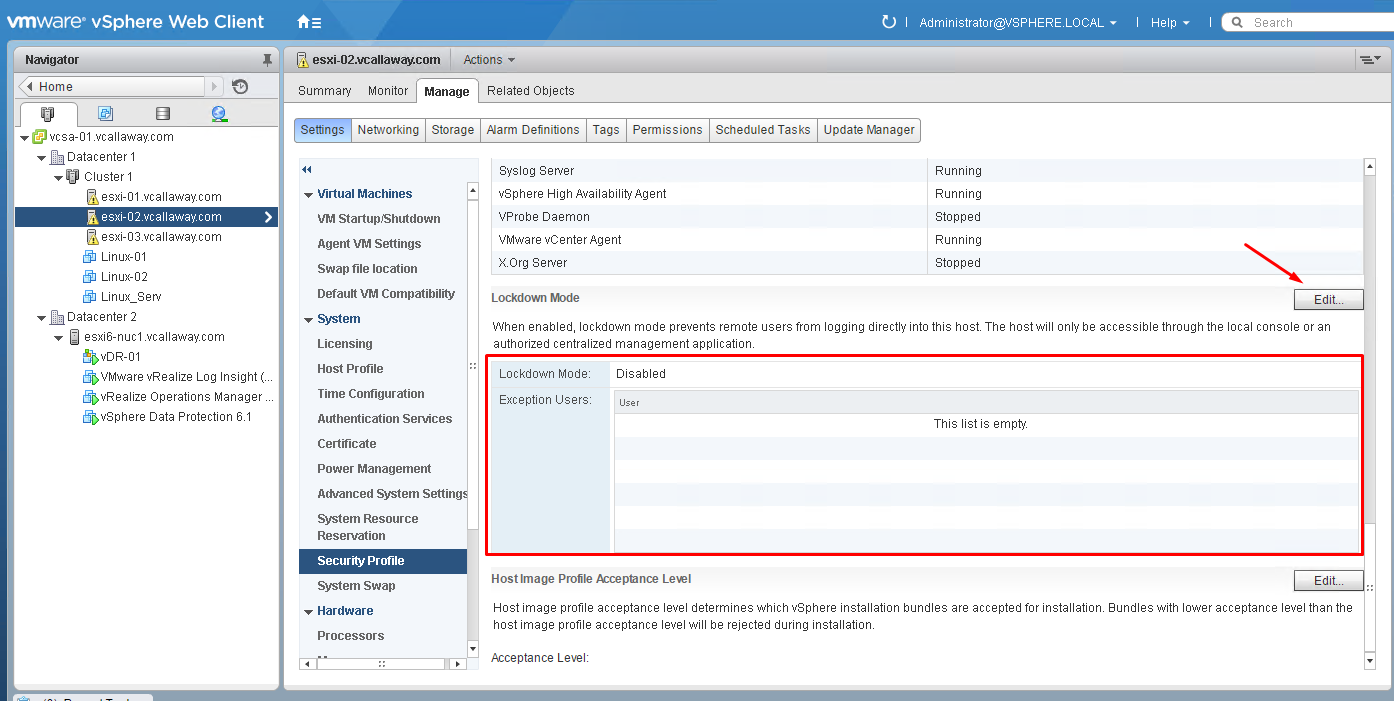
Enable Lockdown Mode
Normal Lockdown mode:
In normal lockdown mode the DCUI service is not stopped. If the connection to the vCenter Server is lost and access through the vSphere Web Client is no longer available, privileged accounts can log in to the ESXi host’s Direct Console Interface and exit lockdown mode. Only these accounts can access the Direct Console User Interface:
- Accounts in the Exception User list for lockdown mode who have administrative privileges on the host. The Exception Users list is meant for service accounts that perform very specific tasks. Adding ESXi administrators to this list defeats the purpose of lockdown mode.
- Users defined in the DCUI.Access advanced option for the host. This option is for emergency access to the Direct Console Interface in case the connection to vCenter Server is lost. These users do not require administrative privileges on the host.
Strict Lockdown mode:
Harden vCenter Server
Control datastore browser access
Create/Manage vCenter Server Security Certificates
Links to reference:
vSphere 6.0 Documentation Center – Certificate Management Overview
Control MOB Access
Use the Managed Object Browser only for debugging, and ensure that it is disabled in production systems.
- Select the host in the vSphere Web Client and go to Advanced System Settings.
- Check the value of Config.HostAgent.plugins.solo.enableMob and change it as appropriate.
Restrict Administrative Privileges
For better logging, associate each permission you give on an object with a
named user or group and a predefined role or custom role. The vSphere 6.0
permissions model allows great flexibility through multiple ways of
authorizing users or groups.
Be sure to restrict administrator privileges and the use of the administrator
role. If possible, do not use the anonymous Administrator user.
See “Understanding Authorization in vSphere,”
on page 114 and
“Required Privileges for Common Tasks,” on page 127.
Understand the implications of securing a vSphere environment
Creating and enforcing security polices and practices adversely affects the ‘convenience’ of users and administrators but having a well defined security posture helps and ensures that proper security practices are followed. The same practices that are valid of typical Windows/Linux systems still apply to a vSphere environment and even more so since that could be the gateway to the entire environment.